Information Security Management System
Huali Group implements stringent information security controls to protect corporate operations and stakeholders from fraud, theft, and other cybersecurity threats.
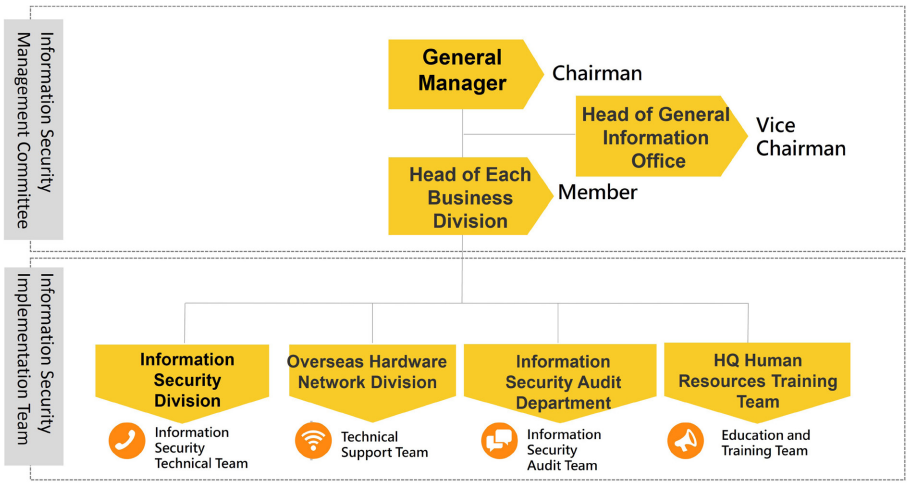
Under the oversight of the Board of Directors and Executive Management, we establishes an Information Security Structure. The General Manager serves as Chair of the Information Security Management Committee, responsible for supervising the development and implementation of information security policies. This committee acts as the highest decision-making body for information security governance, responsible for planning, developing, and coordinating security governance system . Business division heads conduct relevant risk identification and management activities, collaborating with the Information Security Implementation Team to collectively form the information security management system that applies to all employees across group’s business divisions, subsidiaries, and factories.
We establish and implement the Data Lifecycle Management Procedure to safeguard individuals' rights to access, correct, and delete personal data. This enables the progressive establishment of standardized information and privacy governance, mitigates adverse impacts from information leaks or privacy breaches as well as infringement on personnel, and drives persistent efforts toward the secure, reasonable utilization of information privacy.
Information security organization structure
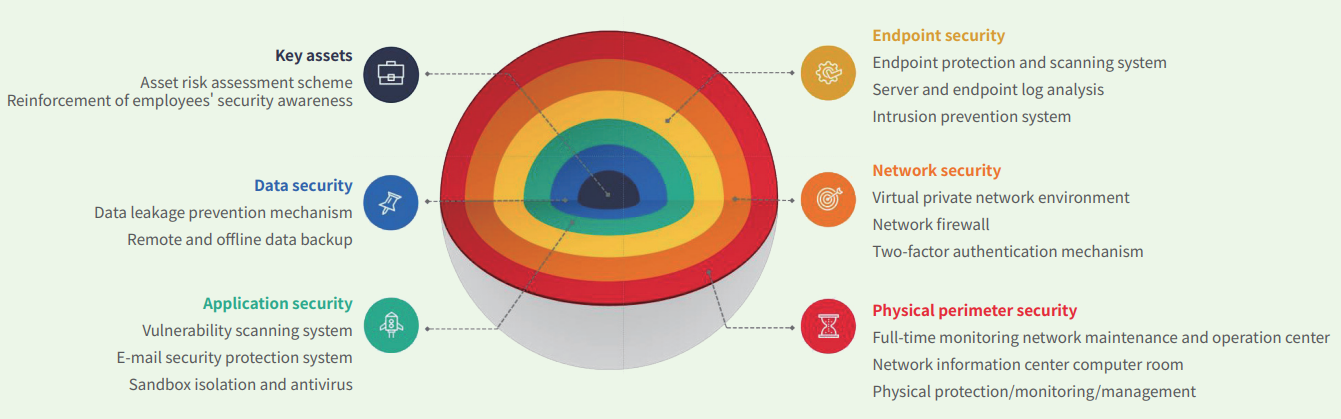
Information Security Technology Protection
Defense-in-Depth
We establish a multi-layered defense mechanism spanning assets, data, systems, networks, and the surrounding environment. This framework is supported by an information security incident reporting and response platform, alongside comprehensive information security management policies.
Our endpoint protection strategy includes Managed Detection and Response (MDR) / Endpoint Detection and Response (EDR) systems and antivirus solutions. These provide robust protection for all critical assets, including servers, workstations, desktops, and laptops. Furthermore, we engage the external, independent information security vendors to conduct regular third-party penetration tests, ensuring the security of our application systems and network infrastructure and enabling continuous improvement in our cybersecurity posture.
Internal Information Management
We maintain rigorous controls over employees' workflows and online activities. Including the implementation of Sangfor Internet Behavior Management solutions to oversee website access, communication tools, and application usage. For securing critical data transfers, our Data Loss Prevention (DLP) system enforces file encryption and blocks unauthorized dissemination via removable storage devices or third-party platforms.
In 2024, we continuously enhanced data leakage prevention through:
1. Deployment of two-factor authentication for SSL VPN access
2. Implementation of external network access restrictions
3. Upgrades to our local network firewall
These measures collectively strengthen the protection of corporate information assets.
Information Security-related Training
To strengthen organization-wide cybersecurity awareness, we mandate comprehensive information security training for all new hires during onboarding. Additionally, our Information Security Department implements sustained awareness initiatives including:
1. Weekly information security meetings
2. Internal phishing simulation drills
3. Targeted training for violators
4. Monthly security bulletins distributed across all factories
These programs equip employees with critical knowledge to identify risks, manage threats, and enhance professional security capabilities.
Throughout 2024, we conducted 160 training sessions covering multiple domains: new employee orientation ,policy compliance, System administration, Network security.
Information Security enhancement Training

To address evolving cyber threats, the Group establishes a Security Operations Center (SOC) platform enabling centralized reporting and management of information security incidents to mitigate potential damages. We establish and publish the Information Security Incident Management Procedure, which implements a four-tiered classification system with corresponding response priorities (Critical, Major, Moderate, Minor) .We also stipulate the time required for response and notification of corresponding levels of incidents, and establish a clear notification process and mechanism.
All employees are required to immediately report security risks and incidents through this standardized mechanism, ensuring timely handling of cybersecurity matters.
More


